In this article, you will understand step by step how to easily integrate with Microsoft Defender
Microsoft 365 and Microsoft Defender users can connect using Azure AD
Integrating with Microsoft Defender and Microsoft 365 will allow Scytale to collect relevant user access information and their access privilege rights on Microsoft. This will help to inspect and ensure that only authorized users have access to Microsoft - which is one of the key criteria when testing logical access. Manually collecting this type of evidence can take some time, especially when you need to prove to the auditors that the user listings are complete and accurate, and when you have a long list of users that require multiple pieces of evidence to be provided.
Automating the collection of user listings and access privileges streamlines the sampling process for the audit, and also provides assurance over the accuracy and completeness of the evidence collected.
Permissions for Microsoft Defender Integration
All the permissions that are required for the integration with Microsoft Defender are read-only permissions and do not allow Scytale to perform any actions within your Azure AD account.
Machine.Read.AllVulnerability.Read.AllAlert.Read.All
How to Connect Scytale and Microsoft Defender
1) In Scytale, go to 'Integrations'.


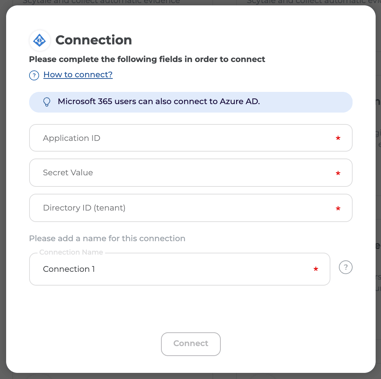
3) Paste the following details into the connection screen:
-
Application ID - learn how to get this below
-
Secret Value - learn how to get this below
Directory ID - B - learn how to get this below
💡Global admin role should create the application.
Step 1: Register an application
-
Log in to the Azure portal and then navigate to Microsoft Defender.
-
On the left menu, click on App registrations
-
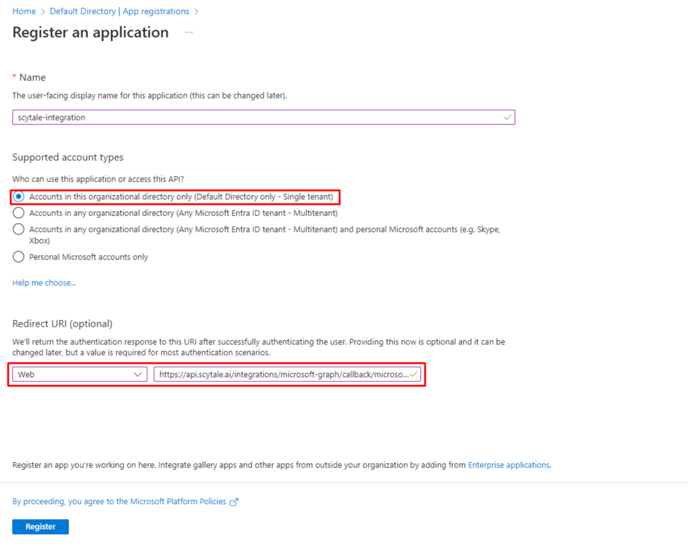
On the screen that loads, click on New registration and fill in the following details:
-
Name - you can choose a name, for example: scytale-integration
-
Supported account types - the first option must be selected - "Accounts in this organizational directory only (Default Directory only - Single tenant)".
-
Redirect URI - select Web from the drop-down menu, and in the text box paste the following:
https://api.scytale.ai/integrations/microsoft-graph/callback/microsoft-graph -
Click on Register
-
-
Next, navigate to the app registrations page.
-
On the app registrations page, click on scytale-integration (the application you just created in the previous step).
-
On the left menu, select "overview".
-
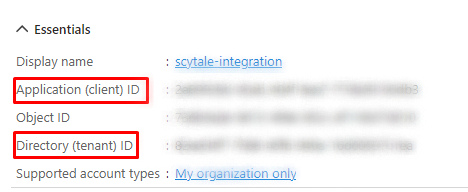
Under "Essentials", copy the (A) - Application (Client) ID and the (B) - Directory (tenant) ID (You'll need this to connect the integration.)
-
Make sure you are still within the scytale-integration app, created in step 1.
-
Go to "Certificates & secrets", in the left menu.
-
Click on New client secret.
-
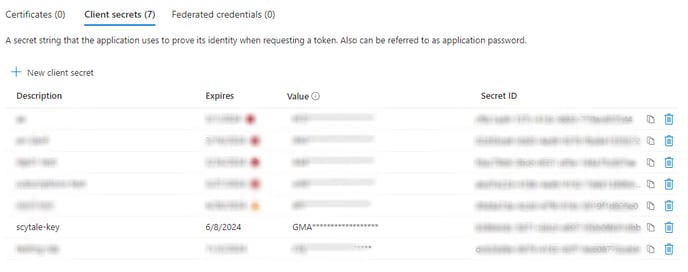
Description - you can choose a description, for example: scytale-key
-
Expires - we recommend selecting 730 days (24 months). As we cannot collect data after the key expires.
-
Click on Add.

-
-
Click on the copy sign on the (C) - "Value" column. (You'll need this to connect the integration)
Step 3: Add permissions
-
Make sure you are still within the scytale-integration app, created in step 1.
-
Go to "API permissions"
-
Click on "Add a permission"

-
Under "Request API permissions"
-
In APIs my organization uses, search for "WindowsDefenderATP" and then select it.

- Next, select "Application permissions"
Select to add the following permissions (you can search for permissions from the list): - Machine.Read.All
- Vulnerability.Read.All
- Alert.Read.All

-
Click on Add permissions

-
Under API permissions - to grant permission, select "Grant admin consent for Default Directory".

